The purpose of this workshop is for participants to become aware of identity theft and the fact that our personal data can sometimes become public on the internet. Participants will also learn how to protect data when needed.
General Objective
Preparation time for facilitator
Competence area
Time needed to complete activity (for learner)
Name of author
Support material needed for training
Resource originally created in
Introduction
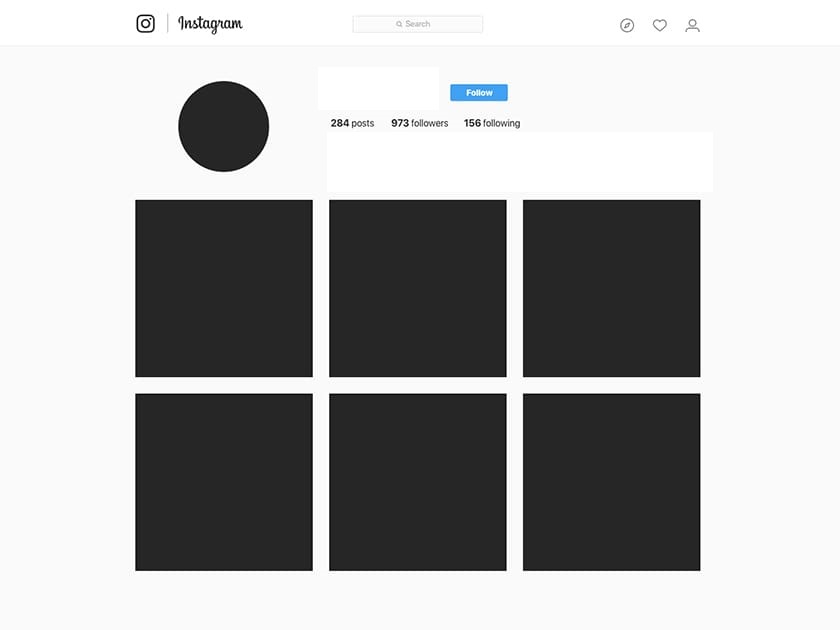
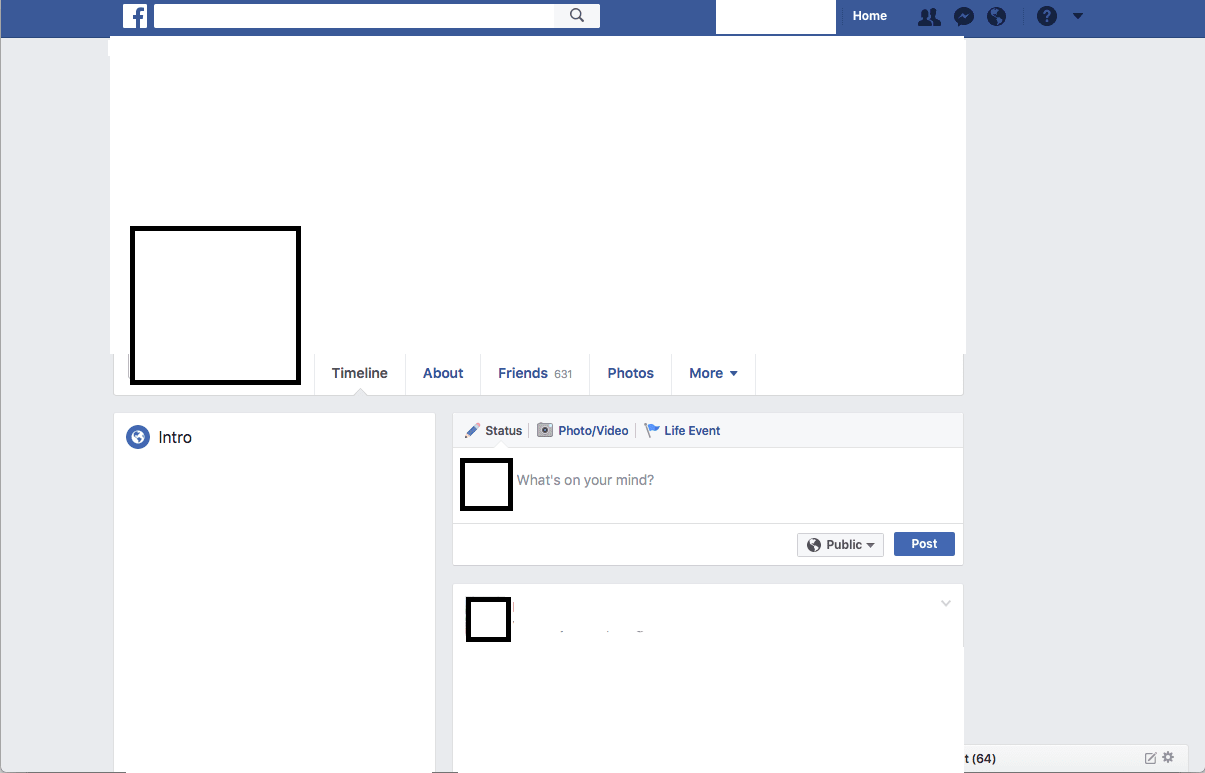
The goal of this workshop is develop awareness of the data that we leave online in a way that it is publicly available. It is meant to emphasise the risks of identity theft. We therefore recommend that you carry out this activity by affirming from the outset that participants should be considerate if they find out some unwanted information about another. However, if during the course of this workshop, some unwanted information is indeed discovered on another participant, it is important to understand that this information is already online, public and available to anyone. It is better that this information be found out in the context of this workshop in order to help the individual concerned to better manage their digital identity. To be done in advance: Print the various blank dating app, Instagram or Facebook profiles in the annex. Depending on the duration of the workshop, give all three blank profiles to each participant or instead, just one example per participant.
Identity Theft
Participants will have to steal the identity of their colleague. Everyone chooses at random the name of another participant. They must now research online, and based on the information found on that the chosen participant, they should attempt as best they can to become an internet doppelganger. This is what we call identity theft. The idea is not that we create actual (fake) Facebook, Instagram or dating app profiles. This would necessitate deleting the accounts at the end of the activity, and it would always be possible that someone forgets. It is thus necessary to have at hand the printed profile mock-ups. Participant A will search information and photos online of participant B – the person whose name they drew randomly. These are therefore public data that a complete stranger could conceivably find without being linked (as say, a friend or folllower) with the person whose identity they seek to steal. If the two participants happen actually to be linked, they must disconnect, for the duration of the activity, from all relevant platforms on which they have an established connection. At this point, based on the things participant A finds on the internet they may be able to compile information such as date of birth, personal details such as interest and even posts and publications shared on social media. They may also be able to print photos if they manage to find any. Leave between 20 and 45 minutes for each participant to search for information, then print and fill in the printed profile. When the time is up, everyone should show what they have come up with. Ask each participant how they found the information and, regarding the fake profile created based on them, if they had realised that all this information could be found.
Emphasising the risks of identity theft
Ask participants what they understand by identity theft. Ask also what it does – what are the consequence for example for the person whose identity we assume? Ideas to respond with: This is a crime that consists of deliberately assuming the identity of another person with the goal of committing fraudulent actions. Such actions and their results vary. The perpetrator may access the financial information of the person whose identity they have taken or indeed commit a crime in that person’s name. They could also create a phone number, a bank account, borrow money or rent a car. Recall that identity theft is punishable by up to ten years in prison in the UK. For more examples, see this article from the New York Times or this public awareness message from Staysmartonline.gov.au.
Going further
After seeing what to do in case you are the victim of identity theft. One of the solutions is to be smarter about password creation. It would make sense therefore to follow the workshop with this one
A possible variant to the present workshop is the following: rather than asking participants to steal each other’s identities, use celebrities instead (YouTubers, rappers, actors, comedians etc.). This solution maybe confuses the goal of the exercise however, considering these people tend be to be public personalities already.
Variation
If you lack time, you can also ask participants to write a story recounting the life of a person whose identity has been stolen. For inspiration, you can direct them to this article from the New York Times.