This workshop is based on a variant of the famous card game UNO. Participants will be guided to better understand certain elements of cybersecurity, for example, the difference between a virus and a computer worm.
General Objective
Preparation time for facilitator
Competence area
Time needed to complete activity (for learner)
Name of author
Support material needed for training
Resource originally created in
Rules of the game
Part 1: Rules of the Game
This is a reflex-based game in which two teams oppose each other, each with 500 points. Each player represents one IT security company that wants to work for a PR corporation. The employees of each company must prove that their security system is better than the other’s. The points represent the important data having to be protected by each team to show the superiority of their security system. When a team gets rid of all their cards, they win. At this point, the opposing team counts the number of points lost that their remaining cards represent (see Part 2 for how to calculate lost points). When a team has no points left, they lose. At the beginning of each game, players receive 7 cards. The rest comprise the draw pile. For every round, the top card on the draw pile is placed face-up to the side. This will now represent the discard pile and the player to play first will base their turn on this one face-up card. When the draw pile is exhausted, shuffle the discard pile and turn it face-down and continue playing. Each player must follow the most recent card played with either the same colour, the same number or the same symbol. If a player does not have a card corresponding to the number, the colour or the symbol, they will have to pick up a card. If they can play the card they just picked up, they may do so. If not, they forfeit their turn. When a player has only one card remaining, they must say UNO. If they forget to say it and an opponent point this out verbally at the beginning of the next turn, the player at fault must pick up two cards. To spice up the game, there are action cards which have special effects on the game:
- Windows update cards: can be used if a player has no playable cards (no cards of the same symbol, number or colour as the most recently played). However, if an opponent thinks that a player had another card that they could have played, they can call the bluff. In this case, the player must show their cards. If the opponent was right, the player must pick up four cards. If they were wrong, it is they who must pick up four cards!
- Hacking cards: when this card is played, the next player must skip their turn.
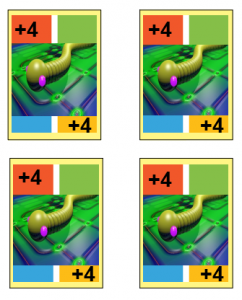
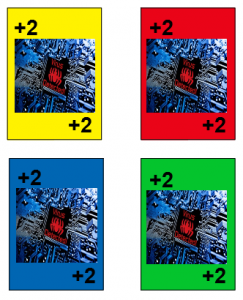
- Virus and Worm cards: the person playing after these are played must pick up the number of cards indicated. This can be avoided by adding instead another one of these cards, meaning, by placing another ‘+2’ card on the previous. The following player will then either have to place another ‘+2’ or pick up 4 cards. Only ‘+2+’ can accumulate!
- Network cards: players using these must exchange their cards with an opposing player of their choice.
We have added other action cards with varying effects to introduce more complexity to the game and broaden the cybersecurity theme:
- Antivirus cards: protects from the effects of ‘+2’ and ‘+4’ cards.
- Phishing cards: a chosen opponent must reveal their hand to the player who uses this card.
- Operator cards: protects from phishing.
Calculating points lost
Part 2: Calculating points lost
Lost points are attributed as follows: Numbered Cards (0-9) Subtract value indicated
Virus cards -20 points
Worm cards -50 points
Hacking cards -20 points
Windows update cards -50 points
Network cards -20 points
Antivirus cards -80 points
Phishing cards -60 points
Operator cards -60 points
Miss a turn -10 points
Game elements
Part 3: Game elements
The game is composed of:
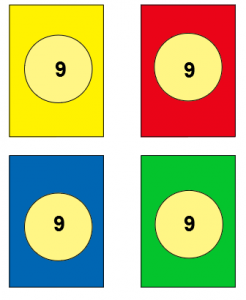
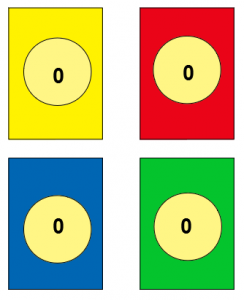
- 19 cards of each colour (red, green, blue, yellow) from 0-9 (2 for every colour, except 0)
- 8 Virus cards
- 8 Hacking cards
- 8 Network cards
- 4 Windows update cards
- 4 Worm cards
- 1 Operator card
- 1 Phishing card
- 1 Antivirus card
To print
To print once:
0 cards:
Worm/’+4′ cards:
Windows update cards
Phishing card:

Antivirus card:

Operator card:

To print twice:
Network cards:

Hacking cards:
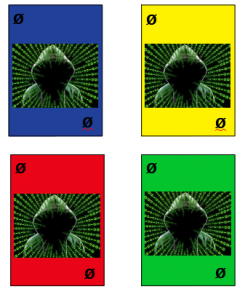
Virus/’+2′ cards:
Cards numbered 1-9: